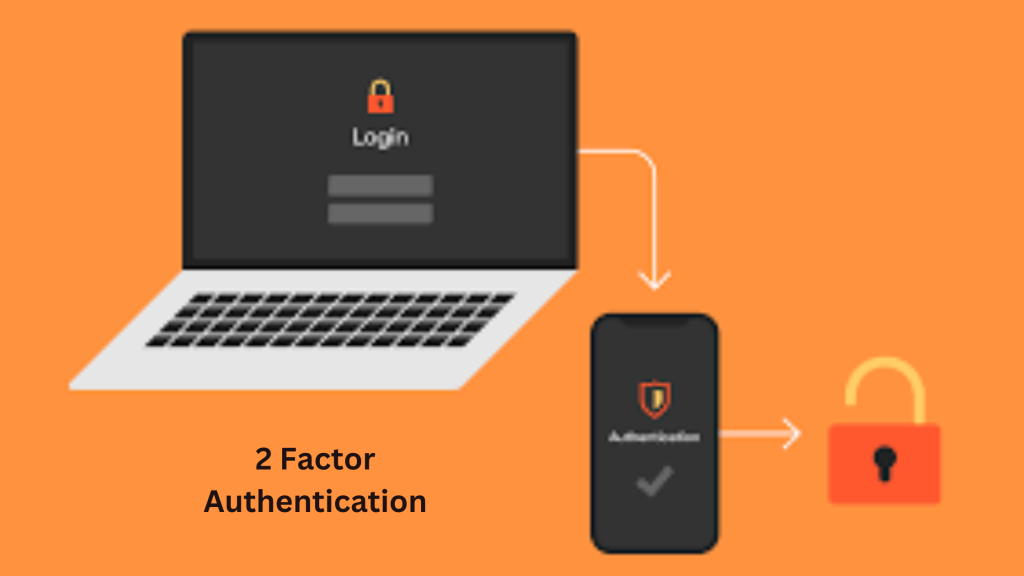
Imagine a fortress with a single gate, secured by a single lock. It may suffice to keep out the casual intruder, but what about the determined thief? In today’s digital age, your personal data is like that fortress, constantly under threat. That’s where Two-Factor Authentication (2FA) comes in – it adds an extra layer of security to safeguard your sensitive information.
In this article, you will delve into the world of 2FA and understand how this powerful defense mechanism works. You will explore the various types of 2FA, from SMS codes to biometrics, and learn which methods are most commonly used.
Moreover, you will uncover the challenges and considerations surrounding this technology, as well as explore the future of 2FA.
Through real-life case studies, you will witness the success stories of organizations that have implemented 2FA effectively. By the end, you will have a comprehensive understanding of 2FA and how it can fortify your digital fortress.

It’s time to take control of your security and lock out the intruders once and for all.
Key Takeaways
- Two-factor authentication (2FA) adds an extra layer of security to protect personal data.
- Implementing 2FA reduces the risk of unauthorized access to accounts.
- Different methods of 2FA include SMS codes, authentication apps, and biometrics.
- 2FA significantly reduces the risk of unauthorized access and protects personal information.
Introduction
Now that you understand the basics of cybersecurity, it’s time to delve deeper into the introduction of two-factor authentication (2FA) and why it’s crucial for protecting your sensitive information.
Two-factor authentication, also known as multi-factor authentication, adds an extra layer of security to your online accounts, making it more difficult for hackers to gain unauthorized access.
It works by requiring you to provide two different types of identification: something you know (like a password) and something you have (like a one-time password generated by a mobile app).

This combination of factors significantly reduces the risk of your accounts being compromised. By implementing 2FA, you can ensure that even if someone manages to obtain your password, they won’t be able to access your accounts without the second factor of authentication.
What is Two-Factor Authentication (2FA)?
Two-Factor Authentication (2FA) is a security measure that adds an extra layer of protection to your online accounts. It requires you to provide two different types of information to verify your identity.
This typically includes something you know, like a password, and something you have, like a unique code sent to your mobile device.
Defining Two-Factor Authentication
Two-Factor Authentication (2FA), also known as two-step verification or multi-factor authentication, is a security measure that adds an additional step to the login process. It ensures that even if someone manages to obtain your password, they still need another piece of information to gain access to your account. Adding an extra layer of security, 2FA requires users to provide two forms of identification, such as a password and a fingerprint, significantly reducing the risk of unauthorized access.

Did you know that 81% of hacking-related breaches occur due to weak or stolen passwords? This statistic highlights the importance of implementing additional security measures like 2FA.
This additional factor could be something you have, like a fingerprint or a physical token, or something you are, like a facial or voice recognition. By requiring two different types of authentication, 2FA provides stronger protection against cyberattacks and helps to keep your sensitive information safe.
How Two-Factor Authentication Works
To enhance your online security, let’s dive into how the process of Two-Factor Authentication (2FA) actually works.
Two-Factor Authentication (2FA) adds an extra layer of security to your online accounts. The first step is logging in with your username and password.

After that, you’ll need to verify your identity using another factor. This can be done in different ways, such as receiving a code via SMS, using a two-factor authentication app, or even a fingerprint scan.
When setting up multi-factor authentication, you’ll go through a step-by-step verification process. Once you’ve completed the initial login, the second factor will be required every time you log in to your account.
This two-step authentication process significantly reduces the risk of unauthorized access and provides an additional level of protection for your personal information.
The Need for Stronger Authentication
If you rely solely on password-only security, you are putting your online accounts at risk. Hackers have become increasingly adept at cracking passwords, and even complex ones are no longer enough to ensure your data’s safety.

That’s why implementing two-factor authentication is crucial. It adds an extra layer of security by requiring not only a password but also a second form of verification, such as a fingerprint or a unique code sent to your phone.
The Limitations of Password-Only Security
Despite our best efforts to create complex and unique passwords, they often crumble under the weight of determined hackers, leaving our personal information vulnerable.
This is where two-factor authentication (2FA) or multi-factor authentication (MFA) comes into play. The limitations of password-only security have prompted the need for an extra layer of protection.
With 2FA, you not only need to enter your password, but also provide a second form of verification, such as a code generated by an authentication app. This additional step significantly reduces the risk of unauthorized access to your accounts.

Google and other authentication app providers offer easy-to-use and secure solutions for implementing 2FA. By utilizing this extra layer of security, you can better safeguard your personal information and ensure that only authorized individuals can access your accounts.
Rationale for Implementing Two-Factor Authentication
Now that you understand the limitations of relying solely on password-only security, it’s time to explore the rationale behind implementing two-factor authentication (2FA).
Two-factor authentication, also known as multi-factor authentication, adds an extra layer of security to protect your online accounts. Its purpose is to greatly reduce the risk of unauthorized access by requiring users to provide not just one, but two forms of identification.
By combining something you know (like a password) with something you have (like a fingerprint or a unique code sent to your phone), two-factor authentication significantly enhances the security of your accounts.

The rationale for implementing this extra layer of security is simple: it greatly reduces the chances of a hacker gaining access to your personal information, financial data, or sensitive documents.
In a world where cyber threats are constantly evolving, two-factor authentication is a crucial step towards safeguarding your online presence.
Types of Two-Factor Authentication
In this discussion, you’ll explore the different types of two-factor authentication that can enhance security.
One type is Knowledge-Based Authentication (KBA). It involves verifying your identity through secret information that only you should know, such as a password or a security question.

Another type is Possession-Based Authentication. Here, you prove your identity by possessing something physical, like a mobile device or a security token.
Lastly, there is Inherence-Based Authentication. This type uses unique biological traits, such as fingerprints or facial recognition, to verify your identity.
Knowledge-Based Authentication (KBA)
By answering personal questions or providing specific information, you can unlock an additional layer of security known as Knowledge-Based Authentication (KBA).
KBA is a type of two-factor authentication that adds an extra layer of security to your online accounts or systems.
It works by asking you to provide information that only you should know, such as your mother’s maiden name, your first pet’s name, or your favorite color.
This information is used to verify your identity and ensure that you are the rightful owner of the account.
By incorporating KBA into your authentication process, you can have a better understanding of who is accessing your accounts and protect them from unauthorized access.
It is an effective way to add an extra layer of security and keep your personal information safe.

Possession-Based Authentication
To enhance the security of your online accounts, you can use possession-based authentication. This method requires you to use something you have, like a mobile phone or smart card, to verify your identity and protect your personal information.
One popular example of possession-based authentication is using the Google Authenticator app. This app generates a unique code that you enter along with your password when logging into your account. The code changes every few seconds, making it nearly impossible for hackers to gain unauthorized access to your account.
Possession-based authentication adds an extra layer of security to your online accounts by ensuring that even if someone knows your password, they would still need physical access to your mobile phone or smart card to log in.
Inherence-Based Authentication
Improve the security of your online accounts by using your unique biological traits, such as fingerprints or facial recognition, to authenticate your identity.

Inherence-Based Authentication, also known as biometric authentication, is one of the methods of authentication used in two-factor authentication (2FA). It adds an extra layer of security by requiring you to provide something you are, in addition to something you have.
Biometric 2FA is more secure than traditional methods because it relies on physical characteristics that are difficult to replicate. With biometric authentication, you can ensure that only you can access your accounts, as your fingerprint or facial features are unique to you.
This advanced technology provides a convenient and reliable way to protect your personal information and prevent unauthorized access to your online accounts.
Common 2FA Methods
In this discussion, you will learn about the common methods used in two-factor authentication (2FA). These methods include One-Time Passwords (OTP), SMS Verification, Authentication Apps, and Biometric 2FA.

One-Time Passwords (OTP) are temporary codes that provide an additional layer of security. They require you to enter a unique code sent to your device.
SMS Verification involves receiving a text message with a code that you must enter to verify your identity.
Authentication Apps, such as Google Authenticator, generate time-based codes for you to enter during the login process.
Lastly, Biometric 2FA uses your unique physical characteristics, like fingerprints or facial recognition, to confirm your identity.

One-Time Passwords (OTP)
One-time passwords (OTPs) are a crucial component of two-factor authentication (2FA) that adds an additional layer of protection to your online accounts. OTPs are temporary codes that are generated on-the-spot and can only be used once. They are typically delivered through various channels such as text messages, email, or authenticator apps.
Time-based OTPs change every few seconds, ensuring that even if a hacker intercepts the code, it will be useless by the time they attempt to use it. Event-based OTPs, on the other hand, are generated in response to specific actions or events, providing an added level of security.
Using an authenticator app for OTP authentication is highly recommended as it offers a more secure and convenient way to generate and manage OTPs.
SMS Verification
Protect your online accounts with an added layer of security by receiving verification codes via text message, ensuring that only you can access your account.

SMS authentication, also known as text verification, is a crucial component of two-factor authentication. It adds an extra layer of security by requiring you to enter a unique code sent to your mobile device.
This method helps prevent unauthorized access even if someone knows your password. When you enable SMS verification, you can rest assured that only you can log in to your accounts. It’s a simple yet effective way to protect your sensitive information.
By understanding the importance of this extra security measure, you can keep your online accounts safe from potential threats.
Authentication Apps
Now that you understand the importance of SMS verification for two-factor authentication, let’s explore another option: authentication apps.
These apps, such as Google Authenticator, Microsoft Authenticator, and LastPass Authenticator, provide an extra layer of security for your accounts. Instead of relying on SMS, these apps generate time-based one-time passwords (TOTPs) that are unique to each login attempt.
Using an authentication app is simple. After enabling two-factor authentication on your account, you’ll need to scan a QR code provided by the app. Once set up, the app will generate a new code every few seconds. When logging in, you’ll be prompted to enter this code along with your password. Since the code changes frequently, it makes it extremely difficult for hackers to gain unauthorized access to your accounts.
Authentication apps are a convenient and reliable way to enhance the security of your online accounts, making them an excellent choice for two-factor authentication.
Biometric 2FA
Biometric 2FA enhances online security by using fingerprint or facial recognition for authentication. It is a form of two-factor authentication that adds an extra layer of security to your online accounts.

Instead of relying solely on a password, biometric 2FA requires a unique physical characteristic, such as your fingerprint or face, to verify your identity. This technology has gained popularity with the rise of smartphones that have built-in fingerprint scanners or facial recognition capabilities.
Apps like Google Authenticator offer this feature, allowing you to use your biometric data to authenticate your identity when logging into your accounts.
By incorporating biometric 2FA, you can significantly reduce the risk of unauthorized access to your personal information, providing peace of mind and better protecting your online presence.
The Advantages of Two-Factor Authentication
Enhance the security of your accounts by implementing two-factor authentication. This method provides an additional layer of protection against potential breaches.

By requiring a second form of verification, such as a fingerprint or a unique code, two-factor authentication significantly reduces the risk of unauthorized access to your personal information.
Enhanced Account Security
Surprisingly, it turns out that adding an extra layer of security to your account can actually make life easier.
Two-factor authentication (2FA) provides enhanced account security by requiring double verification to access your account.
With 2FA, not only do you need to enter your password, but you also need to provide a second form of authentication, such as a unique code sent to your mobile device.

This additional step ensures that even if someone manages to obtain your password, they would still need access to your physical device to gain entry.
By implementing multi-factor authentication, you significantly reduce the risk of unauthorized access to your account, protecting your personal information, financial data, and sensitive communications.
So, embrace the convenience and peace of mind that comes with enhanced account security through two-factor authentication.
Protection Against Password Breaches
Strengthening your account’s security can protect against password breaches. This ensures that unauthorized individuals cannot access your personal information. One effective way to add an extra layer of security is by implementing two-factor authentication. With two-factor authentication, you not only need to enter a password but also provide a second form of verification, such as a fingerprint or a unique code sent to your phone.

This additional step makes it much more difficult for hackers to gain access to your account, even if they manage to obtain your password through a breach. By requiring multiple forms of verification, two-factor authentication significantly reduces the risk of unauthorized access and provides an added level of protection against password breaches.
So, take the necessary steps to enable two-factor authentication and ensure the security of your personal information.
Implementing two-factor authentication significantly reduces the risk of unauthorized access. It makes it 66% less likely for hackers to gain entry into your account. By adding an extra layer of security, two-factor authentication requires users to provide not only their password but also a second form of verification. This can be a fingerprint scan or a unique code sent to their mobile device.
This additional step adds an extra barrier for hackers to overcome. They would need not only your password but also access to your physical device or biometric information. With two-factor authentication, even if a hacker manages to obtain your password, they would still be unable to access your account without the second factor of authentication.

This greatly enhances the security of your online accounts. It protects your sensitive information and reduces the risk of unauthorized access.
Implementing Two-Factor Authentication
When implementing two-factor authentication, there are two key points to consider:
- Websites and online services: First, you need to ensure that the websites and online services you use offer two-factor authentication as an option. This can provide an additional layer of security to protect your personal information.
- Authentication app setup: Second, you will need to set up an authentication app on your device, such as Google Authenticator or Authy, to generate the unique codes needed for the authentication process. This will help prevent unauthorized access to your accounts and keep your information safe.

Websites and Online Services
Websites and online services have become a breeding ground for hackers, but with 2FA, you can protect your sensitive information and feel a sense of peace knowing your accounts are secure.
Two-factor authentication, also known as multi-factor authentication, adds an extra layer of security to your online accounts. One popular method is using Google Authenticator, a mobile app that generates unique codes for each login attempt.
To set up Google Authenticator, you simply need to follow the instructions provided by the platform or website you are trying to secure. For example, Gmail offers a simple and straightforward process for enabling two-factor authentication.
By enabling 2FA and using Google Authenticator, you significantly reduce the risk of unauthorized access to your accounts and ensure that your personal information remains protected.

Authentication Apps Setup
Setting up authentication apps like Google Authenticator is as easy as following a few simple steps on your mobile device, ensuring that your online accounts are protected with an added layer of security.
To start, download the Google Authenticator app from your device’s app store. Once installed, open the app and follow the prompts to set it up.
Next, navigate to the security settings of the online account you want to enable two-factor authentication for. Look for the option to enable MFA (Multi-Factor Authentication) and select it.
Choose the option to use an authentication app and follow the instructions provided. This usually involves scanning a QR code with your phone’s camera.

Once completed, the authentication app will generate unique codes that you will need to enter when logging into your account, providing an extra level of protection against unauthorized access.
Balancing Security and Convenience
When it comes to balancing security and convenience, it’s important to assess the different options for two-factor authentication (2FA) based on your specific use cases. Consider the level of security needed and how it aligns with the convenience factor for each use case.
Additionally, it’s crucial to have recovery options in place for 2FA in case of emergencies or if you lose access to your primary authentication methods.
Assessing 2FA Options for Different Use Cases
When assessing 2FA options for different use cases, you have a few choices.

One option is to use a text message or email verification code, which is convenient but not the most secure.
Another option is a hardware token, which generates a unique code for each login attempt. However, hardware tokens can be expensive and easily lost.
A popular choice is an authenticator app, which generates a time-based one-time password (TOTP) that changes every 30 seconds. This option is convenient, cost-effective, and provides a high level of security.
Assess your needs and choose the 2FA option that best suits your requirements.

Recovery Options for 2FA
Consider having a backup plan in case you lose access to your authenticator app or if it becomes unavailable for any reason. Recovery options for 2FA are essential to ensure you can still access your accounts even if your primary authentication method is unavailable.
One popular option is the recovery code provided by most authenticator apps. This code allows you to regain access to your account by entering it in case your device is lost or the app is inaccessible.
Another option is to link your authenticator app to your phone number or email address. This way, you can receive a verification code through a different channel when needed.
Additionally, some services offer backup codes that you can write down and use as a backup authentication method.

It’s important to enable MFA (Multi-Factor Authentication) for all your accounts, including Google Authenticator, and explore the recovery options available for each.
Encouraging Two-Factor Authentication Adoption
To improve the adoption of two-factor authentication (2FA), consider the following key points:
- User education and awareness: Help individuals understand the importance and benefits of using 2FA. Provide clear information about the risks of not using 2FA and the ease of implementing it. Encourage users to take the necessary steps to protect their accounts.
- Implement 2FA as a standard security measure: Organizations and businesses should make 2FA mandatory for employees and customers. By doing so, businesses can create a culture of security and reduce the risk of data breaches.

By addressing user education, implementing 2FA as a standard security measure, and emphasizing the importance of protecting sensitive data, you can encourage the adoption of two-factor authentication.
User Education and Awareness
Learn how to protect your personal information and keep your accounts secure by understanding the importance of two-factor authentication.
User education and awareness play a crucial role in promoting this extra layer of security. By educating users about two-factor authentication, they become more aware of the potential risks and the need to protect their accounts.
It is essential to understand that using only a password is no longer enough to keep your information safe. Two-factor authentication provides an additional security measure by requiring a second form of authentication, such as a fingerprint scan or a unique code sent to your phone.

This ensures that even if your password is compromised, unauthorized access to your account is prevented.
Stay informed and take control of your online security by implementing two-factor authentication wherever possible.
2FA for Organizations and Businesses
Implementing two-factor authentication (2FA) is a crucial step for organizations and businesses to enhance their security measures. With the increasing number of cyber threats, it is essential to add an extra layer of protection to safeguard sensitive information. 2FA requires users to provide two different types of authentication, typically a password and a unique code sent to their mobile device. This additional step significantly reduces the risk of unauthorized access, as even if a hacker manages to obtain a password, they would still need the second factor to gain entry.
Many companies are now implementing 2FA to protect their data and ensure the privacy and security of their employees and customers. Multi-factor authentication (MFA) is an essential tool for companies and cybersecurity organizations to enhance their security measures. This additional layer of protection is especially important for organizations that handle sensitive data or have a large customer base. By implementing 2FA, organizations can mitigate the risk of unauthorized access and protect their valuable information from potential threats.
Security Considerations and Challenges
In this discussion, you will explore two important aspects of two-factor authentication (2FA): potential vulnerabilities and addressing user resistance.
You will learn about the potential weaknesses in 2FA systems and how attackers can exploit them. Additionally, you will explore strategies to overcome user resistance and promote widespread adoption of 2FA.
By understanding these challenges, you will be better equipped to enhance the security of your online accounts and protect your sensitive information.
Potential Vulnerabilities in 2FA
Beware! Two-factor authentication, while effective, is not an impenetrable fortress; there are potential vulnerabilities that can still leave your accounts susceptible to attackers.

One vulnerability lies in the use of Google Authenticator for PC. Although this tool provides an additional layer of security, it is not completely foolproof. Attackers can still gain access to your accounts if they manage to compromise your PC.
Another vulnerability is seen in Microsoft Multi-Factor Authentication. While it adds an extra layer of protection, it is not infallible. Hackers can exploit weaknesses in the system or use sophisticated techniques to bypass it.
Additionally, two-factor authentication on Apple devices can also be vulnerable. If a hacker gains physical access to your device, they can potentially bypass the authentication process.
To mitigate these risks, consider using a trustworthy multi-factor authentication app that has undergone thorough security testing and regularly updates its security measures.

Addressing User Resistance to 2FA Adoption
Overcoming user reluctance can be challenging, but providing clear instructions and emphasizing the benefits of 2FA adoption can help encourage users to enhance their account protection.
When it comes to two-factor authentication (2FA), some users may be resistant to adopting this extra layer of security. However, it is important to address their concerns and educate them about the advantages of 2FA.
One way to do this is by clearly explaining the process and how it adds an extra layer of security to their accounts. Additionally, highlighting the potential risks of not using 2FA, such as the possibility of unauthorized access or data breaches, can help users understand the importance of adopting this security measure.
By emphasizing the benefits and providing step-by-step instructions, you can help users overcome their resistance and feel more confident about implementing 2FA.

The Future of Two-Factor Authentication
In the future of two-factor authentication, you can expect to see various trends in multi-factor authentication (MFA) that aim to enhance security.
Biometric advancements will play a significant role, as innovative technologies like facial recognition and fingerprint scanning continue to evolve.
These advancements will provide an extra layer of protection by utilizing unique physical characteristics for authentication purposes.
Multi-Factor Authentication (MFA) Trends
With the ever-evolving landscape of technology, the adoption of Multi-Factor Authentication (MFA) continues to rise, fortifying digital security measures with an additional layer of protection. MFA goes beyond the traditional Two-Factor Authentication (2FA) by incorporating multiple factors for stronger security.

One popular method of MFA involves using an authenticator app, which generates a unique code that is required along with the usual username and password. This code is time-sensitive and changes constantly, making it difficult for hackers to gain unauthorized access.
The use of MFA not only provides an extra layer of security, but it also helps prevent unauthorized access in case of stolen or compromised passwords.
As technology advances, MFA will continue to evolve, ensuring that our digital assets remain secure in an ever-changing threat landscape.
Biometric Advancements and Innovations
Now that you’re familiar with the latest trends in Multi-Factor Authentication (MFA), let’s dive into the exciting world of biometric advancements and innovations.

Biometrics, such as fingerprint and facial recognition, are revolutionizing the way we secure our digital lives. By leveraging unique physical and behavioral traits, these cutting-edge technologies provide an extra layer of security to traditional two-factor authentication methods.
Biometrics offer a more secure and convenient way to authenticate your identity, eliminating the need to remember complex passwords or carry physical tokens.
With continuous advancements in this field, we can expect to see even more innovative biometric solutions in the future, such as iris scanning and voice recognition.
Embracing these biometric innovations will ensure that your sensitive information remains protected, adding an unparalleled level of security to your online activities.
Case Studies: Successful Use of Two-Factor Authentication
In this section, you’ll explore notable examples of successful two-factor authentication (2FA) implementation. These real-life case studies will provide valuable insights into how organizations have leveraged 2FA to enhance their security measures and protect sensitive information.
By examining these examples, you’ll gain a deeper understanding of the benefits and practical applications of implementing 2FA. Let’s take a look at some of these successful case studies and see the impact 2FA has had on security incidents and preventing data breaches.
Notable Examples of 2FA Implementation
Explore notable examples of how 2FA has been implemented to add an extra layer of security, and discover how it can keep you protected online.
One popular example of 2FA implementation is the Google Authenticator app. This app generates time-based one-time passwords (TOTPs) that are used as the second factor for authentication. When logging into an account, users must enter their password as the first factor and then input the TOTP generated by the app as the second factor.

Another example of 2FA is multi-factor authentication (MFA), which combines two or more authentication methods. For instance, a user might be required to provide a password, enter a unique code sent to their mobile device, and provide a fingerprint scan.
These examples demonstrate how 2FA strengthens the security of authentication processes, making it harder for unauthorized individuals to access sensitive information.
Impact on Security Incidents and Data Breaches
Boost your online security and protect yourself from data breaches and security incidents by implementing two-factor authentication (2FA). This significantly reduces the risk of unauthorized access to your sensitive information. With 2FA, even if an attacker manages to obtain your password, they would still need the second factor, such as a unique code sent to your mobile device, to gain access.
This extra layer of security makes it extremely difficult for hackers to breach your accounts and steal your data. Research shows that organizations that implement 2FA experience a significant reduction in security incidents and data breaches. By requiring an additional authentication factor, 2FA acts as a strong deterrent against attackers. It makes it much harder for them to compromise your accounts and access your personal information.

Take control of your online security and start using 2FA today to safeguard your sensitive data.
Recap
So, now you understand the importance of two-factor authentication as an extra layer of security. Implementing two-factor authentication significantly reduces the risk of security incidents and data breaches. It requires users to provide two different authentication factors, making it harder for attackers to gain unauthorized access. This additional layer of security acts as a strong deterrent against hackers. Ultimately, two-factor authentication should be considered a crucial step in protecting your personal and business data.
Incorporating two-factor authentication greatly enhances the security of your online accounts and systems. It ensures that your information remains safe and secure.
Frequently Asked Questions
How does two-factor authentication protect against phishing attacks?
Two-factor authentication protects against phishing attacks by requiring users to provide a second form of identification, such as a code sent to their phone. This prevents attackers from accessing your accounts even if they steal your password.

Can two-factor authentication be used for all types of online accounts?
Yes, two-factor authentication can be used for most online accounts. It provides an extra layer of security by requiring you to provide two separate forms of identification, such as a password and a unique code sent to your phone.
Is two-factor authentication mandatory for all users?
Two-factor authentication is not mandatory for all users, but it is highly recommended. Adding an extra layer of security, it helps protect your online accounts from unauthorized access and potential cyber attacks.
Are there any alternatives to two-factor authentication for enhancing security?
Yes, there are alternatives to two-factor authentication for enhancing security. Consider using biometric authentication, such as fingerprint or facial recognition, or password managers with strong encryption to protect your accounts.
What are the potential risks or drawbacks of using two-factor authentication?
The potential risks or drawbacks of using two-factor authentication include the inconvenience of needing an additional device or method, the possibility of device loss or theft, and the risk of phishing attacks.

Conclusion
So there you have it, folks! After diving deep into the world of two-factor authentication, you must be feeling like a security guru now.
Adding that extra layer of protection is like having a superhero sidekick, always ready to save the day.
So go ahead, embrace the power of 2FA and keep those hackers at bay.
Remember, without it, your online accounts are like a fancy car with no doors.

Stay safe, my friends, and happy authenticating!
You might also like to read on these cybersecurity articles on Get Hitch
Protecting Your Digital Privacy: Tips for Safeguarding Personal Information
Recognizing Fake Websites: How to Avoid Online Scams and Fraud